COMPUTER NETWORKS

For most businesses in the United States, computers are an essential part of their daily operations. Many businesses have come to rely on their computers to store and track information, communicate with customers and suppliers, design and manufacture products, and more. It is not uncommon for businesses of all sizes to have multiple computers in an office. Often, these computers are connected through networks that allow information to be shared between computers.
A computer network, as defined in the Merriam-Webster dictionary, is "a system of computers, peripherals, terminals, and databases connected by communications lines." In other words, networks are used to connect computers to other computers, as well as to other devices such as printers, scanners, and fax machines. Networks can be used to connect devices in the same building or they can be used to connect devices that are miles apart. Perhaps the most well known network in use today is the Internet. Many individuals and businesses around the world connect to the Internet on a daily basis. Other examples of networks include library card catalogs, the displays of flight arrival and departure times used at airports, and credit card readers at retail stores.
NETWORK CONFIGURATIONS
Networks can be set up in a number of different ways depending on the number of devices, the distances between those devices, the transmission speed requirements, and other factors. The most popular configurations, or topologies, include the bus, token ring, star, and star bus topologies.
BUS.
With a bus configuration, each node is connected sequentially along the network backbone. A node is any device connected to the network, such as a computer, printer, or scanner. Backbone is the term used to describe the main cables to which the network segments are connected. Resistors are placed at each end of the network to ensure that the signal is terminated when it reaches the end. When one node sends information to another node through the network, the information travels along the backbone until it reaches the desired receiving node.
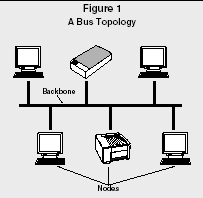
A Bus Topology
TOKEN RING.
With a ring configuration, each node is connected sequentially along the network backbone. However, unlike the bus configuration, the end of the network connects to the first node, forming a circuit. Nodes on a token ring take turns sending and receiving information. In the token ring topology, a token travels along the backbone with the information being sent. The node with the token sends information to the next node along the backbone. The receiving node reads the information addressed to it and then passes the token and any additional information to the next node. This continues until the token and data make it back to the first node in the network.
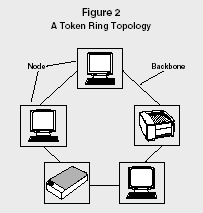
A Token Ring Topology
STAR.
With a star configuration, each node is connected to a central hub via network segments. When one node sends information to another node, the information passes through the hub. The hub does not filter or route the information in any way; it simply serves as a connector between network segments.
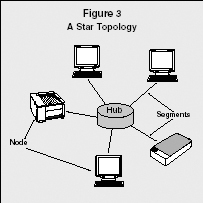
A Star Topology
STAR BUS.
With a star bus configuration, the hubs of multiple star networks are connected together via the backbone. This is the most common network configuration in use.
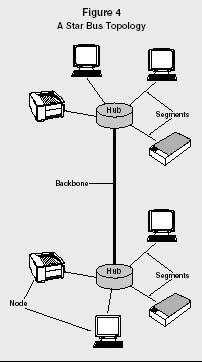
A Star Bus Topology
LOCAL AREA NETWORKS AND WIDE
AREA NETWORKS
A local area network (LAN), as the name implies, is a network that connects devices that are local, or relatively close to each other. Nodes on a LAN are usually in the same building. A wide area network (WAN), on the other hand, is used to connect nodes that could be miles apart. LANs generally transmit data faster than WANs, and they are usually more reliable. Fiber-optic cables are used for both LANs and WANs.
ETHERNET NETWORKING.
Ethernet is a LAN protocol (i.e., a set of rules that governs communications) developed in the mid-1970s by Bob Metcalfe and David Boggs at Xerox Corporation's Palo Alto Research Center. Today, Ethernet is the most widely used network technology in the world. The original Ethernet used a bus topology and provided for transfer rates of up to 10 million bits per second (Mbps). This Ethernet specification was modified slightly and became the Institute of Electrical and Electronics Engineering (IEEE) 802.3 standard, which helped solidify Ethernet as a widely-recognized, open international standard. The IEEE 802.3 specifies the physical networking interface and lower layers of software usually associated with Ethernet. Vendors ship an estimated total of 300 million Ethernet ports each year.
Although networks using Ethernet protocol generally connect devices over short distances, technological advances now allow Ethernet to connect devices that are miles apart. Ethernet is widely accepted and largely installed because it is simple and efficient and because network interface cards (NIC) for Ethernet can be easily installed in personal computers, workstations, or high-end computers. Furthermore, it can run on a variety of media, including fiber optics, twisted-pair, cable, and wireless connections.
REPEATERS.
When Ethernet was first implemented, most people used a copper coaxial cable. However, the maximum length of this cable was 500 meters, which was not long enough for some networks. To address this problem, network engineers used repeaters to connect several Ethernet segments.
BRIDGES.
Bridges provide a simple means for connecting LANs. A bridge is a device that connects physically separate LAN segments (such as different Ethernet cables) into one logical LAN segment. There are four categories of bridges: transparent, source routing, encapsulating, and translating. Transparent bridges are used for Ethernet, whereas source routing bridges are used for token ring networks. Encapsulating bridges connect two segments of the same media (such as token ring to token ring) over a medium. The receiving bridge removes the envelope, checks the destination, and sends the frame to the destination device. Translating bridges are used to connect different types of network media such as Ethernet and FDDI (fiber distributed data interface). FDDI is a set of protocols that uses a modified form of the token-passing method over fiber-optic cable.
ROUTERS.
LAN segments joined by a router are physically and logically separate networks. In contrast to a bridge, when multiple network segments are joined by a router they maintain their separate logical identities (network address space), but constitute an internetwork.
Routers specify the destination and route for each packet, and they can be used to direct packets and interconnect a variety of network architectures. A major difference between a bridge and a router is that the bridge distinguishes packets by source and destination address, whereas a router can also distinguish packets by protocol type. Routers provide for the interfaces to WANs such as frame relay and packet switching services. Some new bridge products have added router capabilities; hence, the practical distinction is becoming blurred, giving rise to the term "brouter."
Routers can also be used to limit access to a network by the type of application (e.g., allowing electronic mail to pass, but not file transfer traffic). This capability provides a measure of security for the network, and is used extensively when creating firewalls. Firewalls are implemented to secure an organization's network when it is linked to the Internet.
SWITCHES.
Ethernet communicates across the network using the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) process. A protocol using CSMA/CD monitors, or listens to, the media for network traffic, or information traveling through the network from one node to another. If a node does not sense any traffic, it will send frames or packets of information onto the media. A network frame is like a mailed letter. The letter is put in an envelope that has a return address and the address of its destination. Data are like the letter and the frame is like the envelope. The data is placed in the frame and the frame has the addressing information and error-checking code. Each protocol has its distinctive frame. The device continues sending until it finishes or until a collision occurs.
A collision happens when more than one device transmits data at the same time. When a collision occurs, each device waits a random amount of time before trying to retransmit the data. By having each node wait a random amount of time, there is only a slim chance that the two devices will send out the data at the same time again. The collision detection and frame retransmission are part of the protocol.
One way to reduce the number of collisions is to add switches to the network. A switch, like a hub, connects nodes to each other. However, while a hub requires each node to share the bandwidth (i.e., the amount of simultaneous data traffic the network can support), a switch allows each node to use the full bandwidth.
In a fully switched network, each node is connected to a dedicated segment of the network, which in turn is connected to a switch. Each switch supports multiple dedicated segments. When a node sends a signal, the switch picks it up and sends it through the appropriate segment to the receiving node. Ethernet protocol in a fully switched environment does not require collision detection because the switches can send and receive data simultaneously, thus eliminating the chance of collision.
Most companies do not use fully switched networks, as the cost of replacing each hub with a switch can be expensive. Instead, most use a mixed network configuration in which a combination of hubs and switches are used. For example, all of the computers in each department may be connected to their own departmental hub, and then all of the departmental hubs may be connected to a switch.
ETHERNET ADVANCEMENTS
The dominance of Ethernet as a LAN technology for desktop PCs has made it difficult for other technologies to gain acceptance. Ethernet technology continues to evolve as Ethernet vendors develop techniques to increase bandwidth and the support of more complex network configurations. For example, Fast Ethernet technology was developed to provide for increased bandwidth of up to 100 Mbps, ten times faster than the original Ethernet. When migrating from Ethernet to Fast Ethernet, a company may need to change network interface cards and the central wiring hub, and it may also need to upgrade the wiring.
In May 1996 eleven network vendors (including Cisco Systems and Sun Microsystems) formed the Gigabit Ethernet Alliance. The goal of the alliance was to develop a standard for 1 Gigabit per second (Gbps) Ethernet transmissions. Soon thereafter, network vendors were successful in designing networks that achieved the 1 Gbps transmissions goal, and in 2002 the IEEE approved the fibre-only 10 Gbps Ethernet. Throughout 2004 great progress was made in the development of l0 Gbps Ethernet technology and its infrastructure. The increased speed of the 10 Gbps Ethernet in terms of data storage, system backup, teleconferencing, and surveillance systems will prove beneficial to blade servers, networked enterprise switches, video servers, and other applications. The higher density, reduced power, and improved cost-effectiveness appeal to all of the major system developers.
Another development in Ethernet technology is power over Ethernet (POE), which the IEEE published in July 2003 as the 802.3af standard. PowerDsine
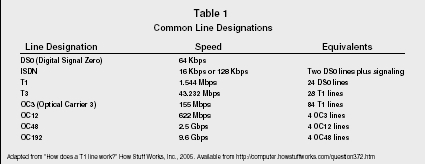
Common Line Designations
| Line Designation | Speed | Equivalents |
| DS0 (Digital Signal Zero) | 64 Kbps | |
| ISDN | 16 Kbps or 128 Kbps | Two DS0 lines plus signaling |
| T1 | 1.544 Mbps | 24 DS0 lines |
| T3 | 43.232 Mbps | 28 T1 lines |
| OC3 (Optical Carrier 3) | 155 Mbps | 84 T1 lines |
| OC12 | 622 Mbps | 4 OC3 lines |
| OC48 | 2.5 Gbps | 4 OC12 lines |
| OC192 | 9.6 Gbps | 4 OC48 lines |
came up with the idea for POE in 1998 and convinced 3Com, Intel, Mitel, National Semiconductor, and Nortel Networks to promote this technology. One of the main purposes of POE is to standardize connections to portable and remote devices that no longer need AC line power. POE can be used for a number of applications, including digital cameras, security systems, and smart sensors.
NETWORK REMOTE ACCESS DEVICES
Network remote access devices are used to connect remote (off-site) users to an organization's network. There are many options available. See Table 1 for some of the common line designations.
MODEMS.
A modem is a device that converts data from digital to analog signals so it can travel over the public switched telephone network (PSTN) to its destination. Once the signal reaches its destination, the modem converts it back to digital. As the PSTN was designed to carry voice (analog signals), it is not the best option for carrying data. Digital data networks (DDNs) are replacing the PSTN. DDNs are used to transmit both data and digitized voice. Because of their slow data transmission speeds, modems are no longer used in most business environments.
ISDN.
Integrated services digital network (ISDN) is a switched, high-speed data service. ISDN is an international telecommunications standard for transmitting voice, video, and data over digital lines running at 64 Kbps, and reaches 1.5 Mbps in North America and 2 Mbps in Europe. ISDN uses the same copper telephone lines as modems do, but at a rate approximately five times faster. Furthermore, it is extremely reliable.
T1.
A T1 line carries data approximately 60 times faster than a modem on a normal telephone line. The higher speed and extreme reliability make this a popular choice for many medium- to large-sized businesses. T1 lines can handle hundreds of users simultaneously for general browsing. However, it cannot handle that many users simultaneously downloading large files, such as MP3 files or video files. For very large companies, T1 lines may not be sufficient.
CABLE MODEMS.
A cable modem is a device used to connect a computer to a coaxial cable, such as the kind used for cable television, in order to access online services. This device modulates and demodulates signals like a conventional modem. In addition, a cable modem functions like a router designed for installation on cable television networks. The most popular application for cable modems is high-speed Internet access, which provides much faster service than standard telephone-line modems, thus enabling users to access streaming audio, video, and other services.
WIRELESS TECHNOLOGY.
Mobile telephones, laptop computers, and handheld computers are so affordable that they have become a part of everyday life for many people and businesses around the world. Advances in wireless technology have made it possible for people to access networks without having to physically connect to the network through cables. For example, it is not uncommon for business travelers to access networks on their wireless fidelity (Wi-Fi)-enabled laptop PCs or handheld computers while waiting at an airport.
Bluetooth is a wireless standard developed by a group of electronics manufacturers to allow any electronic device—such as computers, cell phones, keyboards, and headphones—to find and connect to other devices without any direct action from the user. The devices find one another and transmit data without any user input at all. Because Bluetooth technology is inexpensive and does not require the user to do anything special to make it work, it is gaining wide use around the world.
Wireless products are now affordable and very reliable. With wireless connections, it is possible for people to move around while connected to a network. This could be very useful in environments such as hospitals, so that health care professionals could access patient records from various locations around the campus. Many home and small-business users also use wireless networks to avoid the need to route twisted-pair wiring around their premises. In fact, domestic, small-office, and home-office networking accounts for most of the wireless Ethernet equipment sales in the United States.
In summary, computers connected with communications networks improve productivity and profitability by enabling people and organizations to develop closer relationships with coworkers, customers, business partners, and other people in general.
SEE ALSO: Computer Security ; The Internet
Badie N. Farah
Revised by Rhoda L. Wilburn
FURTHER READING:
Black, Uyless. ATM Volume III Internetworking with ATM. Upper Saddle River, NJ: Prentice Hall, 1999.
FitzGerald, J., and A. Dennis. Business Data Communications and Networking. 6th ed. New York: John Wiley & Sons, 1999.
Franklin, Curt. "How Bluetooth Works." How Stuff Works, Inc. Available from < http://electronics.howstuffworks.com/bluetooth.htm >.
Horn, Keith. "10-Gbit Ethernet Is Ready, along with its Customers." Electronic Design, 23 August 2004, 18.
"How Does a T1 Line Work?" How Stuff Works, Inc. Available from < http://computer.howstuffworks.com/question372.htm >.
Marsh, David. "Ethernet Keeps Pumping the Data." EDN, 14 October 2004, 63.
——. "Power and Wireless Options Extend Ethernet's Reach." EDN, 11 November 2004, 67.
Panko, Raymond. Business Data Communications and Networking. 2nd ed. Upper Saddle River, NJ: Prentice Hall, 1999.
Pidgeon, Nick. "How Ethernet Works." How Stuff Works, Inc. Available from < http://computer.howstuffworks.com/ethernet.htm >.
Stamper, David A. Business Data Communications. 5th ed. New York: Addison-Wesley, 1999.
Tyson, Jeff. "How LAN Switches Work." How Stuff Works, Inc. Available from < http://computer.howstuffworks.com/lan-switch.htm >.
Vargo, J., and R. Hunt. Telecommunications in Business. Chicago: Irwin, 1996.
my TC/IP RANGE START 192.16.8.1 TO 254 BUT HOW TO 50 CONNECT PC SAME NET WORK PLEASE GIVE ME PLAN
THANKS
LAXMANSINGH